Short of Google sending out reps to personally root and rom your phone, I'm not sure what you expect them to do?
Is that a service provided by the AF VIP membership program?
Upvote
0
Short of Google sending out reps to personally root and rom your phone, I'm not sure what you expect them to do?
Yeah, my objection was the charge that I was excusing Google - I was simply not excusing the sensationalism in the press. You don't have to like me or how I roll, but I got enough problems with what I do without being accused of things I don't do. You got a problem with the whole update scheme? You ought to, I agree.I have a Samsung Galaxy Tab 7 running 4.1.2 and i use Boat Browser.
I have an LG phone running 2.3.5 but i only use it for talk and text.
Sorry that you are upset by my comments. But as one of millions of affected Android users, it bothers me when these issues arise. And without notice or warning from google or OEM.
The Android OS/Ecosystem starts at the top with Google. Google should take responsibility and deal with the fragmentation issue. I have been posting and telling friends for years, if you are going to buy an android device, stick with a Nexus. With any other android brand, you cannot trust that the device will be supported. Otherwise when problems arise, you have to go on the internet and try to test or fix, device by device, app by app, or in this case, browser by browser.
BTW, I tested the iPad 3 iOS 8.1.2 on the csc.cyberoam site. I pushed "test app", but nothing happens. Does that mean the ipad is not vulnerable or that the test does not work on the ipad?
Or from now on, stipulate that non-Nexus devices should stick a warning on the box, like on cigarette packages: "This Android device may not receive full support or updates like a Nexus". That is the truth.
Why not let us know?
If there is a safety issue with your car, the manufacturer should warn or recall. If we are warned, we can stop using the device, find an alternative or buy a new one. But if we are left in the dark and lose valuable personal info or suffer economic loss, who will be responsible? Or from now on, stipulate that non-Nexus devices should stick a warning on the box, like on cigarette packages: "This Android device may not receive full support or updates like a Nexus". That is the truth.
I'm especially interested in a Maxthon test. They were identified as having the problem some time back and they claim a big market share.
I don't know what to make of that, it's a different popup from this -
Boat browser = vulnerable
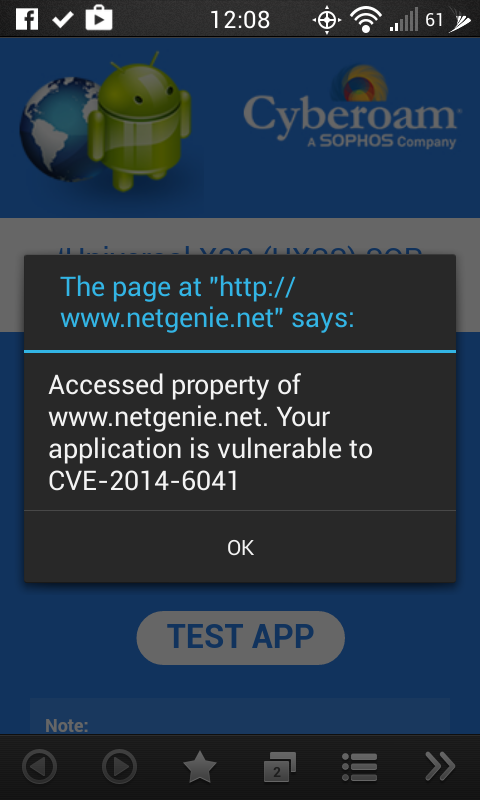
IF this doesn't point back to Google as the responsible party to fix their shit, then I don't know who's in charge of Android.
.
Is there any proof that this is 5.0.1 Lollipop, are we just taking your word for it? Why is the notification bar obfuscated? Maybe because the notification bar icons is usually a give away as to what Android version it is.
It often takes me a few attempts to press the screenshot combo successfully, so a lot of my screenshots have the volume bar in them too.
Also the volume icons/bar, the soft buttons a long the button and the toast show it's Lollipop.
And that's the latest, same as I'm running.
Following public discussion of vulnerabilities in versions of Webkit last week, I’ve had a number of people ask questions about security of browsers and WebView on Android 4.3 (Jellybean) and earlier. I want to provide an update on what we’re doing and guidance on steps that users and developers can take to be safe, even if your device is not yet running Lollipop.
Keeping software up to date is one of the greatest challenges in security. Google invests heavily in making sure Android and Chrome are as safe as possible and doing so requires that they be updated very frequently. With Google’s assistance, Android device manufacturers (OEMs) have been moving rapidly to improve the rate that devices are updated and to ship devices with the most recent versions of Android. We provide patches for the current branch of Android in the Android Open Source Project (AOSP)[https://source.android.com/] and directly provide Android partners with patches for at least the last two major versions of the operating system.
Improving WebView and browser security is one of the areas where we’ve made the greatest progress. Android 4.4 (KitKat) allows OEMs to quickly deliver binary updates of WebView provided by Google, and in Android 5.0 (Lollipop), Google delivers these updates directly via Google Play, so OEMs won’t need to do anything. Until recently we have also provided backports for the version of WebKit that is used by Webview on Android 4.3 and earlier. But WebKit alone is over 5 million lines of code and hundreds of developers are adding thousands of new commits every month, so in some instances applying vulnerability patches to a 2+ year old branch of WebKit required changes to significant portions of the code and was no longer practical to do safely. With the advances in Android 4.4, the number of users that are potentially affected by legacy WebKit security issues is shrinking every day as more and more people upgrade or get new devices.
There are also steps users and developers can take to mitigate the risk of potential exploitation of WebKit vulnerabilities without updating to Lollipop. Using a browser that is updated through Google Play and using applications that follow security best practices by only loading content from trusted sources into WebView will help protect users.
When browsing on any platform, you should make sure to use a browser that provides its own content renderer and is regularly updated. For instance on Android, Chrome [http://goo.gl/elSkZX] or Firefox [http://goo.gl/Q5X6e3] are both great options since they are securely updated through Google Play often: Chrome is supported on Android 4.0 and greater, Firefox supports Android 2.3 and greater. Chrome has been the default browser for all Nexus and Google Play edition devices since 2012 and is pre-installed on many other popular devices (including Galaxy devices from Samsung, the G series from LG, the HTC One series, and the Motorola X and G), so you may already be using it.
Using an updatable browser will protect you from currently known security issues, and since it can be updated in the future it will also protect you against any issues that might be found in the future. It will also allow you to take advantage of new features and capabilities that are being introduced to these browsers.
If you are an application developer, there are also steps you should take to keep users safe. Application developers should make sure that they are following all security best practices[http://goo.gl/b6a3ta]. In particular, to resolve this issue when using WebView[http://goo.gl/FKeouw], developers should confirm that only trusted content (e.g. loaded from a local source or over HTTPS) is displayed within WebViews in their application. For maximum security when rendering content from the open web, consider providing your own renderer on Android 4.3 and earlier so that you can keep it up to date with the latest security patches.

 ) and is being developed by a group of engineers at the Intel Open Source Technology Center http://01.org but also sees contributions from Samsung (Tizen support etc).
) and is being developed by a group of engineers at the Intel Open Source Technology Center http://01.org but also sees contributions from Samsung (Tizen support etc).We've been tracking upcoming products and ranking the best tech since 2007. Thanks for trusting our opinion: we get rewarded through affiliate links that earn us a commission and we invite you to learn more about us.






