Google addressed stagefright specifically, with lead engineer for Android security Adrian Ludwig stating to
NPR that "currently, 90 percent of Android devices have a technology called ASLR enabled, which protects users from the issue."
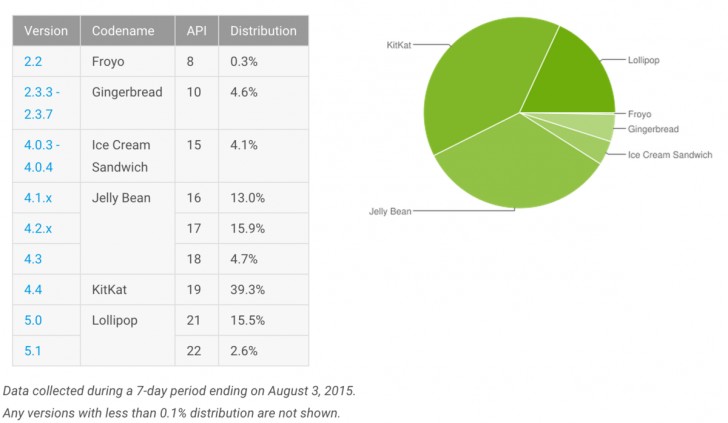
This is very much at odds with the "900 million Android devices are vulnerable" line we have heard. While we aren't going to get into the midst of a war of words and pedantry over the numbers, what Ludwig was saying is that devices running Android 4.0 or higher have protection against a buffer overflow attack built in.
ASLR (
Address
Space
Layout
Randomization) is a method that keeps an attacker from reliably finding the function he or she wants to try and exploit by random arrangement of memory address spaces of a process. ASLR has been enabled in the default Linux Kernel since June 2005, and was added to Android with Version 4.0 (
Ice Cream Sandwich).
How's that for a mouthful?
What it means is that the key areas of a program or service that's running aren't put into the same place in RAM every time. Putting things into memory at random means any attacker has to guess where to look for the data they want to exploit.
This isn't a perfect fix, and while a general protection mechanism is good, we still need direct patches against known exploits when they arise.
Google, Samsung (
1), (
2) and
Alcatel have announced a direct patch for stagefright, and Sony, HTC and LG say they will be releasing update patches in August.